
From Dante’s Inferno to repeat offenders — what do epic poetry and fraud have in common? And what fraud prevention strategies can modern businesses adopt to escape the hellfire circle of identity fraud rings?
A lot has changed since the 14th century, particularly the advent of computers. But the attitude toward fraud has not. The most famous fraud ring, which predates computers and the internet, is arguably found in Dante Alighieri’s epic poem, The Divine Comedy.
The first part of the Divine Comedy is Inferno, detailing Dante’s journey through the nine circles of hell, guided by the poet Virgil. The circles of hell are depicted as concentric, gradually increasing in wickedness, and it is in the eighth circle — before the ninth and final circle where the devil himself resides — where we find the Hell of the Fraudulent and Malicious.
After he arrives upon the monster Greyon (himself the personification of fraud, possessing the face of an honest man, but the tail of a scorpion) Dante meets the occupants of the ditches that make up the eighth circle; Barrators, Counsellors of Fraud, Falsifiers, Imposters, Counterfeiters and Thieves. The latter endure their own identity theft as punishment for stealing people’s identities and possessions in life.
Fast forward 700 years and the fraud rings of today are still made up of imposters, counterfeiters, and thieves, working with an arsenal of cybertools to attack and defraud, creating hell for consumers in the digital economy and challenges for fraud ring detection processes. Fraud rings are perpetrators of identity fraud, attacking people’s livelihoods, their life-savings, and violating and stealing the very thing that makes individuals unique — their identity.
What are identity fraud rings?
Whereas in Inferno the Fraudulent and Malicious are separated by ditches, each experiencing their own punishment, today we see fraudsters working together, in vast hyper-connected networks. They traverse regions, devices, locations, identities, and industries. In fact, they have evolved and become so organized that they mirror legitimate enterprises.
Identity fraud rings are defined as organizations that perform activities with the intention to defraud or take advantage of other people.
Our CEO, Mike Tuchen, explores the concept of a 'fraud corporation' in more depth in his piece for Forbes: Meet The Organizations Built To Exploit You: Stopping Fraud Corporations. In his article, Mike explains a scenario where the fraudster organization’s department recruits money mules from social media, while research & development evolve and innovate attacks, working out, for example, how to apply Remote Access Attacks on mobile devices after seeing their success on desktop devices. The marketing department can run ad scams or operate vast email phishing campaigns, while there are even call centers running number-spoofing scams. Make no mistake, they are organized, smart, connected and constantly innovating.
Not only are they organized, but they know where to put their efforts. Normally they opt for the path of least resistance where they can cash out with minimum effort on their part.
What you need to know about identity fraud rings
According to recent data from the Federal Trade Commission (FTC), American consumers reported losing nearly $8.8 billion to fraud in 2022, with imposter or identity theft scams accounting for $2.6 billion in losses.
While individuals can easily carry out their own identity theft attacks, groups of fraudsters have the ability to share resources and commit fraud on a much larger scale. Whereas individual fraudsters can “shoulder surf” in public places to steal on-screen credentials or send phishing emails to capture identifying information, fraud rings enjoy a much larger net to commit their crimes.
These crimes can include forgery, filing false claims, identity theft and manipulation, and the counterfeiting of checks or currencies. Fraud rings most commonly target an individual’s identity, their credit card information, insurance policies, or even their checkbook. Common examples of fraud ring activity include:
- Stealing multiple pieces of personal identifying information (PII), which are used to create synthetic identities that fraudsters can leverage to make purchases or take out lines of credit
- Laundering money through the theft of credit card information and purchase of gift cards or luxury items
- Staging automobile accidents or falsifying the work done on a vehicle to increase the insurance claim on a “collision.”
When working in unison, members of a fraud ring can inflict tremendous damage on an individual or a business. In 2021, for example, a North Carolina man led a synthetic identity fraud ring in the falsification of credit cards to defraud area banks of more than $400,000. During the COVID-19 pandemic, an identity theft fraud ring in Massachusetts wrongfully obtained more than $135,000 in benefits by stealing the identities of more than 19 individuals.
Detecting fraud rings is harder than it looks, as evidenced by the hundreds of thousands — and sometimes, millions — of dollars in damage inflicted on individuals, companies, and governments. But fraudsters running these rings can be sloppy in their efforts, with one goal in mind — making as much money as possible, as quickly as possible.
Fraud ring detection: The warning signs
From simple fraud in Inferno to easy, scalable attacks today
Drawing on another parallel with Inferno, where the Fraudulent and Malicious were punished because they were all guilty of ‘Simple Fraud,’ today's fraudsters are similarly leveraging low sophistication fraud and scalable attack methods.
In Onfido’s 2023 Identity Fraud Report, ‘low-sophistication’ fraud has surged by 37% year-over-year. Why? Well, it’s easy to enact and is characterized by simple, subtle tweaks to document numbers or identity information like name or date of birth. Fraud rings leverage these ‘low sophistication’ identity attacks with ample resources and manpower to quickly scale attacks on platforms and services en masse.
Fraud is most successful when it can avoid detection. Unfortunately for the fraudsters operating identity fraud rings, businesses have the tools at their disposal to quickly detect anomalies or changes in a regular pattern. For example, a spike in traffic from a set of IP addresses or a surge in the sale of a particular item can raise alarms. Tech-savvy individuals are even coming up with ways to identify fraud rings through social media by linking online communities to one another.
Repeat information, repeat faces, repeat fraud
Choosing quantity over quality and working 24/7, fraud rings can make hundreds, if not thousands of copies of the same document, but tweak minor details each time.
For example, the documents might all have the same face and personal information, with the exception of the document number, which changes by one number each time the document is submitted anew. Or vice versa; the document numbers might all be the same, but the name on the document varies each time.
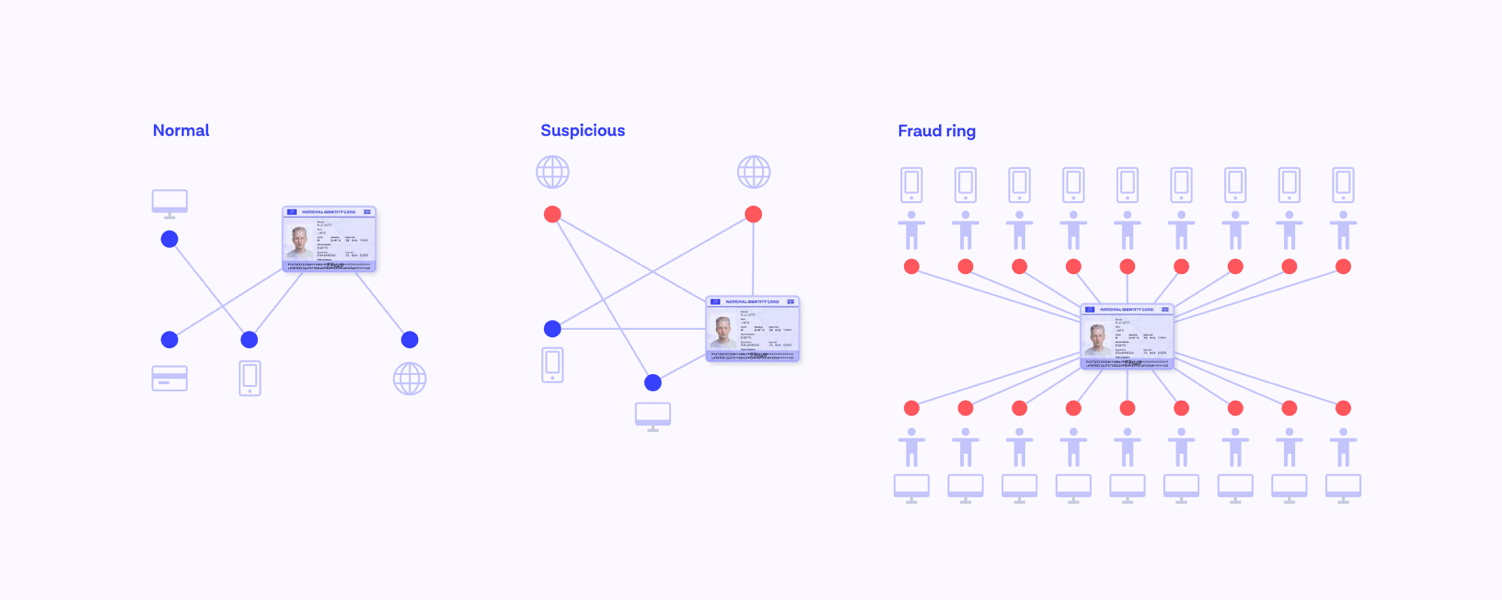
This kind of repeatable fraud is a considerable threat — not just the attack in and of itself; simple, easy to scale, and easy for businesses to miss — but this type of fraud takes resources and manpower away from other, more sophisticated attacks which are likely to result in much bigger fraud losses.
When fraud ring detection is needed, what can businesses protect against low sophistication, repeatable fraud, as well as the fraud rings who are leveraging such attacks at scale?
What to do if you fall victim to identity fraud rings
The ramifications of identity theft can be severe. It is estimated that the global financial cost of fraud is $5.38 trillion, and that number is made up of millions of crimes that occur every year. When an individual’s identity is stolen, it can ruin their livelihood, impact their reputation, and cause irreparable damage. The FTC provides a direct line of communication for identity theft reporting, while most major credit card issuers allow for fraud alerts and credit freezes to stop the theft before it can really take hold. Other institutions, like banks, mortgage lenders, and insurance companies, also enlist fraud departments to protect their patrons.
How to protect from identity fraud rings
A multi-layered approach to fraud detection is a necessity in today's complex, cybercrime landscape and for fraud ring detection. Businesses need to be able to dial up defenses in response to emerging threats and new regulations, all while preserving a seamless user experience for end users. For scalable, repeat fraud, businesses need to compare new applications to historic onboarded data.
Onfido’s Repeat Attempts looks at document data, comparing what has been submitted with what has been seen historically in order to detect repeat ID document use. It was with Repeat Attempts that one leading payments company identified 95 fraud rings in just three months, with the same document number having been submitted 300 times with different attributes.
However, as we know, when fraudsters hit a blocker on one path, they are quick to adapt and attack another. If a solution like Repeat Attempts stops them on the document side, they will likely move efforts and try to spoof the biometrics, or try to infiltrate another touchpoint on the customer journey. Fraud really is a real-life game of whack-a-mole. Layering a solution like Repeat Attempts with a solution like Onfido’s Known Faces, that compares the submitted photo ID with hundreds of thousands of historic faces already onboarded, provides a robust, formidable offense against repeat offenders — chief among them, fraud rings. Layering in this solution is a strong approach for fraud ring detection.
Fraudsters are also heavily deterred by biometric verification. According to our latest report, 83% fewer attacks occurred on biometrics compared to documents, suggesting fraudsters focus their attacks on documents when attempting to bypass onboarding defenses, and abandon attempts when confronted by biometric verification.
For more ways to detect and prevent fraud, take a look at our blog: Detecting fraud — three steps to success.
Does the punishment fit the crime? Tackling identity fraud head-on
There is one last startling difference between the Fraudulent and the Malicious in Inferno and today’s fraudsters. In Inferno, they were being punished for their awful deeds, whereas today’s fraudster landscape is making it difficult to convict those who cause considerable harm through fraud.
In the UK, just 4,924 fraud offenses resulted in a charge last year out of more than 5 million scams reported by victims. This equates to just 0.1% of all fraud resulting in prosecution. With fraud prosecutions at less than one in 100, the failure to fight fraud could actually be luring more criminals to it, which is why we in the industry must band together, collaborate, share insights and fraud data. Becoming a cohesive network of fraud fighters to take on the organized networks of fraud rings with robust fraud ring detection is the best chance we have of successful fraud prevention.
Download our Identity Fraud Report to get the latest insights into the techniques that fraudsters are using to attack your business.





