Businesses need to know who their customers are — for reasons ranging from fraud protection to meeting compliance requirements. But in an increasingly digital world, online identity verification needs to go beyond simply asking their name and a few details. That’s why identity proofing is a necessary step in establishing that the person on the other side of the screen really is who they say they are. Identity proofing solutions make sure that the identity being claimed is the true identity of the individual, by checking multiple sources. Identity proofing online can range from checking data sources to document checks to biometric verification.
What is identity proofing?
Identity proofing is the process a business undertakes to prove the identity someone is claiming in an online transaction. While broader identity verification can use multiple layers of checks, identity proofing refers to the most stringent of checks to prove the identity. Asking a user for personal identifying information (PII) or knowledge-based questions is sometimes used for identity verification, but since another individual can provide this information, it isn’t the most secure level of ID proofing. Identity verification also checks other requirements like age or geolocation.
Identity proofing solutions like document verification that is then matched to biometric verification (a selfie photo or video liveness check) can give reasonable certainty that the user is really who they claim they are.
The identity proofing process is commonly done at onboarding to establish a trusted identity.
A guide to identity proofing
To implement identity proofing solutions, you'll need to assess the best options for your business. Specifically, you should ask yourself what is the goal of identity proofing for your business? It could be to meet compliance regulation or fight fraud or a combination of those and other factors. You will also want to think of a digital identity verification strategy. Also, you need to learn what kind of identity proofing methods are available? And, how to select from identity proofing vendors, and what criteria to asses against.
Download the Guide to Digital Identity Verification to discover how the identity verification landscape has shifted and where the future of onboarding is heading.
What does identity proofing mean?
Proving an identity must go beyond claiming an identity with a name, or an ID document or information. A business must be sure that the claimed identity matches the actual identity — that is, who the person behind a screen really is. Identity proofing services can accomplish this by making sure the person presenting an identity document is the actual owner — with a biometric check. The identity proofing process then gives a high assurance and trust in the user’s identity.
An introduction to identity proofing
Read on to learn all about the different kinds of digital identity verification solutions including identity proofing, different examples of how to do identity proofing, and what kind of things to think about when creating an identity proofing solution for your business.
What's the difference between identity proofing and authentication?
Identity proofing and authentication are both ways of checking who a user is, with the key difference being at which stage of the relationship the check is done. ID proofing is most commonly necessary at onboarding or establishing a relationship. A business must make sure that this identity exists (is genuine, not fraudulent) and being presented by its rightful owner, by asking the claimant to provide more information (most strongly, biometric verification that matches the ID document).
Authentication, on the other hand, is for a returning user. A business must continually check that the user requesting access is the same one who created the relationship.
Let’s look at a common example of when both identity proofing and authentication might be used: when accessing a bank account. Because financial institutions are part of a regulated industry and subject to compliance requirements, they must conduct know your customer (KYC) checks as part of broader AML (anti-money laundering) regulations. This means ensuring a new customer is legitimate and can prove they own the identity they are claiming.
Later, the customer may log back into the account they created, and perhaps transfer an amount over $10,000. Higher-risk moments commonly trigger an authentication request, checking that the user is the same owner of the account who proved their identity when they opened it. The authentication process will verify the user again, asking for information or a biometric verification, to regain access.
What are some examples of identity proofing?
There are many industries and many moments in which a business may need to do online identity proofing on a customer, for reasons ranging from fraud protection to mandatory compliance requirements. Some examples of these moments are when a new customer wants to open a bank account, when someone is renting a car, or traveling through airport security.
The electronic identity proofing process can take many forms, and they range from less reliable, to more high assurance.
Identity proofing examples
-
Personal identifying information (PII)
A business can ask a user to supply information about themselves that ideally only they should know, like their Social Security number (SSN), other personal data, or secret questions like their mother’s maiden name. The problem with this method of identifying someone is that other people could know the information, from spouses, to hackers who bought leaked data from the dark web. It’s not the most secure way to ‘prove’ someone’s identity.
-
Document verification
A user might also be asked to do identity proofing to back up their claim of an identity (like giving a name), with a government document like a photo ID. Since this is a unique and official document, only the person claiming the document should have it. But ID documents can be stolen, tampered with or created by fraudsters. So it’s not enough “proof” of that person’s identity to simply receive an image of a photo ID.
-
Biometric verification
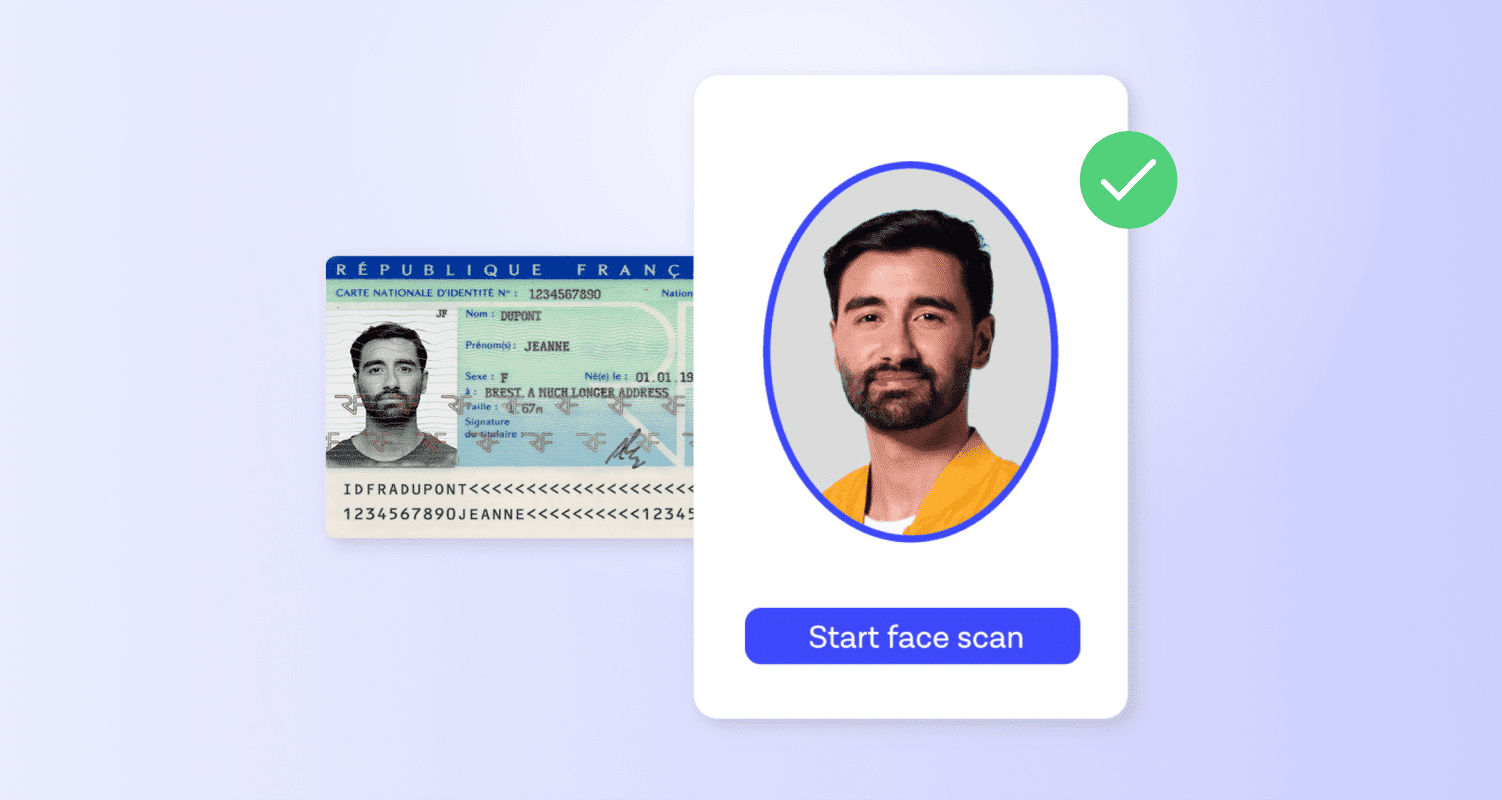
Asking a user to verify their biometric identity and checking that it matches the picture in an ID document is considered the most reliable way to identity proof a digital user. Biometric verification can range from fingerprints, iris scans of the eye, voice imprints, or probably most commonly, a facial recognition scan.
Pairing facial recognition verification with document verification of a government-issued photo ID can weed out fraud attempts and stolen or synthetic identities. It’s a reliable identity proofing method because the person presenting an ID must prove they are the same person by showing their face in their device’s camera for a selfie picture, or a video liveness check.
Modern identity verification technology uses lightening-fast artificial intelligence (AI) to automate checking that a document is genuine, and match facial biometrics to an ID with minimal bias.
Why identity proofing is essential
The importance of identity proofing ranges from the absolute necessity of compliance regulations — such as AML and KYC needs for regulated industries like financial services — to the need to protect your business against fraud by ensuring you have users you can trust.
Identity proofing vendors can help put these protections in place, and prevent reputational and financial damages. Compliance regulations span from the local to global and can be complicated, and violations could result in high fees. And fraudsters are more active and sophisticated than ever, looking for ways to exploit weaknesses in identity verification processes.
Our Identity Fraud Report is full of the latest trends, predictions, and insights taken from our own data. Learn how fraudsters are attacking, and how best to protect your business.
Fast, fair and accurate identity proofing
Onfido enables identity proofing that helps your business navigate compliance, protect against fraud, without negatively impacting your customer’s experience. The Real Identity Platform features a comprehensive Verification Suite, so you can choose the checks you need all in one place, and Onfido Studio lets you build custom journeys with no-code, drag-and-drop orchestration. All powered by Atlas™, our award-winning AI, which returns fast, fair and accurate results in seconds — so that you can know who is really behind the screen, and make digital identity simple for you and your customer.
Our interactive tour walks through our end-to-end identity proofing platform, and features a walk through of how to start building workflows in a free trial of Onfido Studio.






